Archive for the ‘Technology’ Category
Since the time Amazon made a tabbed interface popular, web designers have been talking about the design pattern. Are tabs good? Are they bad? How do you make them?
Amazon has since removed tabs from their site, but it’s still a useful metaphor when done right. So what’s right and wrong? The Usability Post shares 5 tips for tabbed navigation:
- Connect the active tab to the content
- Make other tabs a different color
- Change the font color on the active tab
- Have the link area span the whole size of the tab
- Make sure the landing page has its own active tab
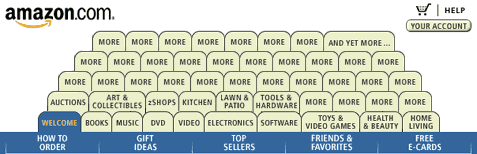
Each step is illustrated with the right and wrong way, and explained. That’s helpful. Now you can include tabs on your website without the wrath of the entire design community (you’ll never avoid all the wrath, no matter what you do). Just don’t look like Amazon in 2000:
If you’d like to implement tabs and don’t know how to do them, you can’t miss with this classic A List Apart tutorial.
Posted by //
Sean
Date //
Aug 22, 08 - 2:48 pm
Categories //
Open Source
Software
Technology
Comments Off on Mozilla Unleashes TraceMonkey For Firefox
 In a move to make Firefox more competitive with desktop applications and proprietary graphics technology like Microsoft Silverlight and Adobe Flash, Mozilla on this afternoon released TraceMonkey.
In a move to make Firefox more competitive with desktop applications and proprietary graphics technology like Microsoft Silverlight and Adobe Flash, Mozilla on this afternoon released TraceMonkey.
TraceMonkey is a project that adds native code compilation to SpiderMonkey, Mozilla’s JavaScript engine.
Mozilla has included TraceMonkey in an alpha version of Firefox 3.1, the next major release of the open-source Firefox Web browser.
TraceMonkey is off by default, because it’s not entirely bug-free but when it’s more stable and enabled, Firefox’s JavaScript should get faster “by an order of magnitude or more,” as Mozilla CTO Brendan Eich put it in a blog post:
“If you’re doing something like image processing, we can demonstrate six to seven times speed-ups and we can probably double those,” said Eich in a phone interview. “If you’re doing a tight [programming] loop that’s just manipulating bits, you can go 20 to 40 times faster.”
Trace Monkey was built with the help of UC Irvine research scientist Andreas Gal, using a technique called “trace trees.”
Mike Schroepfer, VP of engineering at Mozilla (soon to leave for Facebook), has posted a screencast demo that shows how TraceMonkey makes image editing done through Firefox competitive with dedicated image editing applications, at least in terms of the responsiveness of the user interface.
“What we’re trying to do is extend the capability of the browser,” said Eich, adding that graphics applications and games in particular stand to benefit from improved JavaScript performance. “Not everyone wants to get a plug in,” he said.
Improving browser performance is necessary to provide an open-source alternative to proprietary rendering technologies. “If browsers are only doing JavaScript and doing it slowly, we worry that content will migrate to closed platforms like Silverlight,” said Eich.
Mozilla’s support for the canvas graphic rendering element in the HTML 5 specification and the Ogg video format also reflects this goal.
If Mozilla is successful in its efforts, the rationale for developing rich Internet applications (RIAs) will become increasingly questionable. As Eich sees it, RIAs are already at risk. “Those platforms that are not a browser are an increasingly thin value-add to what the browser can do,” he said.
Eich said that when Google launched Google Maps and found that it was done without plug-ins, they were stunned. He expects that ongoing browser performance improvements will usher in similarly surprising applications.
Firefox 3.1 should be ready before the end of the year, Eich said.
Posted by //
Sean
Date //
Aug 21, 08 - 10:45 am
Categories //
Hacking
Security
Technology
Comments Off on FEMA Phones Get Hacked
 If you are going to hack a phone system, do you really want to hack the Department of Homeland Security?
If you are going to hack a phone system, do you really want to hack the Department of Homeland Security?
That’s what happened this weekend when someone made hundreds of illegal calls from a FEMA PBX to the Middle East and Asia.
It appears that it was the usual culprits of poor change control and misconfigurations left FEMA’s digital doors open.
All of this is according to an Associated Press story I read on MSNBC.com last night.
According to the AP’s Eileen Sullivan and Ted Bridis, the attacker placed more than 400 calls on the hacked FEMA phone system to places such as Afghanistan, Saudi Arabia, India and Yemen.
Here’s the kicker, from an IT security perspective, from the AP story quoting a FEMA spokesperson:
FEMA’s chief information officer is investigating who hacked into the system and where exactly the calls were placed to. At this point it appears a “hole” was left open by the contractor when the voicemail system was being upgraded, Olshanski said. Olshanski did not know who the contractor was or what hole specifically was left open, but he assured the hole has since been closed.
This illustrates an excellent, yet often overlooked, point. Despite all of the attention we spend focusing on zero-day vulnerabilities and exotic exploits and attacks – many times it’s simply poor change control procedures, lack of urgency to patch, or carelessness that gets an organization bitten.
Fortunately, in this case, it only appears to have been $12,000 in illegal calls to the Middle East and Asia, and some egg of the face of FEMA and the DHS.
Posted by //
Sean
Date //
Aug 21, 08 - 8:30 am
Categories //
Microsoft
Software
Technology
Comments Off on More Proof Microsoft Is Stuck In 90s: Seinfeld Ads
In case there was any doubt that the company is still stuck in the 1990s, Microsoft hired Jerry Seinfeld as the face of its $300 million USD advertising campaign to hawk Windows Vista.

Here’s the incomprehensible part: The 54-year-old washed-up has-been was chosen because Microsoft is “weary of being cast as a stodgy oldster by Apple Inc.’s advertising,” according to the Wall Street Journal.
Seinfeld is most famous for his 90s-era sitcom, which always prominently displayed a Macintosh in his TV apartment. Microsoft will pay Seinfeld $10 million.
Palm accidentally uploaded a presentation about the Palm Treo 850 — aka Treo Pro — to a public Palm Web site, where it was spotted by bloggers and posted just about everywhere.
It is probably the best looking Treo ever but is that really saying all that much? It sure looks nice:
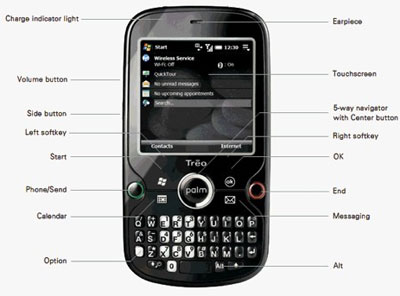
You can see additional pictures of it here and here.
Looks to have either a black or gun-metal finish to it, with nice sharp lines and clean buttons. My one issue is that it still looks chubby.
Palm Treos, even the latest 800w, are a lot thicker than the competition. Motorola, Samsung, Apple, and even RIM seem to know how to make thinner smartphones.
Other details that can be discerned from the presentation are that it will have a full 3.5mm headset jack for headphones, Wi-Fi and of course a touch screen, which all Palms have.
It also looks like it will run the Windows Mobile 6.1 platform and will have a micro-USB jack for transferring data.
When this device will launch is unknown, but it will be with a carrier such as T-Mobile or AT&T, because the first version of it will have GSM / UMTS radios.
This phone is a nice improvement for Palm in the looks department.
Since the next generation of Palm’s own operating system is not going to be available for a while, Palm needs to do its best with Windows Mobile phones if it is to remain relevant in the competitive smartphone market.
Posted by //
Sean
Date //
Aug 12, 08 - 1:05 pm
Categories //
Google
Security
Technology
Comments Off on Google Says Infected Spam Is Getting Worse
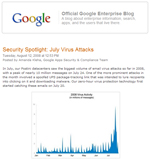 On its enterprise blog this afternoon, Google reported that it saw more infectious spam messages in July than any month so far this year.
On its enterprise blog this afternoon, Google reported that it saw more infectious spam messages in July than any month so far this year.
According to data gathered by Google’s Postini corporate e-mail security service, the volume of e-mail virus attacks peaked at almost 10 million on a single day, July 24.
That kind of volume, six to seven times what’s typical, means spam messages are getting through someone’s defenses and turning recipient’s machines into zombies, said Sundar Raghavan, a product marketing manager with the Google Apps Security & Compliance team.
“The summer of spam has caught up with us this time,” said Raghavan.
Raghavan suggests that in contrast to the message protection Google delivers from the Internet cloud, anti-spam hardware appliances that don’t update fast enough may allow malicious e-mail attacks to succeed.
Much of the spam that Google is seeing aims to exploit not browser or operating system vulnerabilities but user curiosity. Thus, explained Raghavan, spam now takes the form of spoofed CNN newsletters with link descriptions designed to bait the user, such as “Microsoft Bribes Chinese Officials.” Clicking such links in spam messages, however, generally leads to malware.
Raghavan also said that Google has seen an increase in e-mail messages with viruses concealed as encrypted .RAR attachments, despite an overall decrease in malicious attachments.
Marshal, an e-mail security company, this morning issued its security report covering the first half of 2008. In the first six months of 2008, the company says that spam volume doubled.
Marshal said that because of unpatched browsers, 45% of Internet users are at risk when they visit legitimate Web sites hosting malicious code. And there are many such sites. In May, the company identified 1.5 million Web sites infected with malware as a result of a botnet attack.
It may not come as a shock that Marshal, as a maker of e-mail security hardware, has more faith in e-mail security hardware than Google.
“We are now in the situation where spam accounts for almost 90 percent of all e-mail and increasingly contains links to infected sites,” said Bradley Anstis, VP of products, in a statement. “Companies really need to employ a combination of e-mail security gateways that have anti-spam protection using multiple techniques to block malicious content and secure Web gateway products that do not just rely on URL filtering but also scan the content that end users are downloading and uploading in real-time.”
E-mail users may also want to consider in-brain message filtering (no purchase required). Just as one might be skeptical of offers of wealth from a mysterious Nigerian benefactor, one might also refrain from clicking on links to suspect news stories along the lines of “Steve Jobs Uses Windows Vista At Home” or “Google Provides NSA With Real-Time Search Data.”